The global serverless architecture market attained a value of USD 8.79 billion in 2023. The serverless architecture market is further expected to grow in the forecast period of 2024-2032 at a CAGR of 27% to reach USD 77.23 billion by 2032. As serverless computing continues to gain traction in the world of technology, it has become increasingly crucial to address the security challenges associated with this innovative approach to application development and deployment.
Serverless computing offers numerous benefits, including cost efficiency, automatic scaling, and reduced operational overhead. However, with these advantages come unique security risks that organizations must understand and mitigate to protect their functions and data. In this comprehensive blog post, we will explore serverless security best practices that can help safeguard your serverless applications.
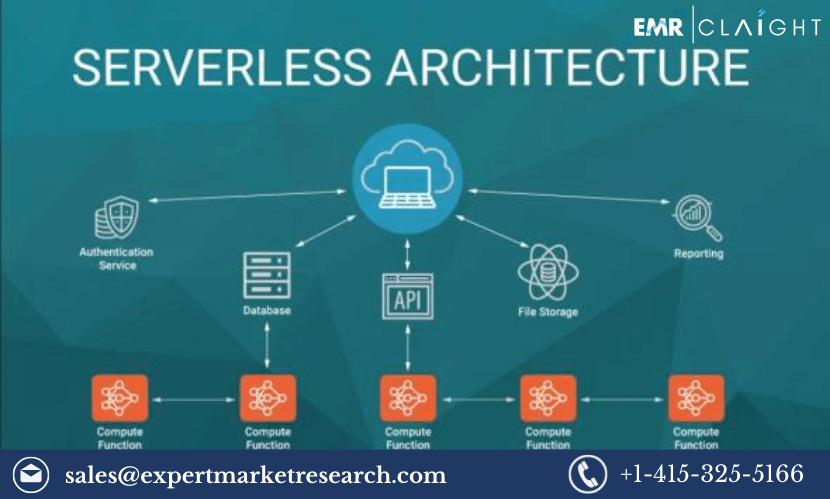
Serverless computing has revolutionized the way businesses build and deploy applications. In a serverless architecture, developers focus on writing code (functions) while the cloud provider takes care of infrastructure management. This abstraction, while efficient, introduces new security considerations.
To secure your serverless applications effectively, it’s essential to understand the unique security challenges they pose. These challenges include:
Get a Free Sample Report with Table of Contents@ https://www.expertmarketresearch.com/reports/serverless-architecture-market/requestsample
Traditional security measures designed for monolithic applications may not suffice in serverless environments. The dynamic nature of serverless functions and event-driven architectures requires a different approach to security.
Implement the principle of least privilege (PoLP) by granting only the minimum permissions necessary for each function to perform its intended task. This reduces the attack surface and limits potential damage.
Leverage Identity and Access Management (IAM) policies provided by your cloud provider to define and enforce access control. Assign roles with specific permissions to functions based on their requirements.
Implement role-based access control (RBAC) to ensure that only authorized users or services can invoke functions and access resources. Regularly review and update access permissions.
Use encryption protocols such as HTTPS and TLS to protect data while it’s in transit between your serverless functions and external services or clients.
Encrypt data at rest using services like AWS Key Management Service (KMS) or Azure Key Vault. This safeguards your data even when it’s stored within the cloud provider’s infrastructure.
Implement secure coding practices by conducting regular code reviews. Look for common vulnerabilities like injection attacks, broken authentication, and insecure dependencies.
Validate and sanitize input data to prevent injection attacks. Use input validation libraries and frameworks to ensure data integrity.
Integrate vulnerability scanning tools into your CI/CD pipeline to automatically identify and remediate security issues in your serverless code.
Set up comprehensive logging to monitor the execution of your functions. Log critical events and activities, making it easier to detect anomalies and threats.
Use centralized log management services like AWS CloudWatch Logs and Azure Monitor to aggregate and analyze logs from multiple functions and services.
Configure real-time alerts to receive notifications when security-related events occur. Proactive monitoring helps in swift incident response.
In addition to native security features provided by cloud providers, consider using third-party security tools and services designed specifically for serverless applications. These tools can enhance your security posture by offering advanced threat detection, compliance monitoring, and more.
Datadog provides a comprehensive monitoring and security platform that helps organizations gain visibility into their serverless environments. It offers features such as anomaly detection and real-time alerts.
Twistlock is known for its container security capabilities but has extended its support to serverless. It helps organizations identify vulnerabilities, enforce security policies, and protect serverless functions.
Serverless Framework offers a wide range of plugins that can enhance the security of your applications. Explore available plugins for security scanning, secret management, and more.
Regularly conduct penetration testing to identify vulnerabilities in your serverless applications. Engage security experts to simulate attacks and assess your defenses.
Encourage secure coding practices through peer code reviews. Focus on identifying and addressing security issues during the development phase.
Implement continuous security assessments as part of your CI/CD pipeline. Automate security testing to catch vulnerabilities early in the development lifecycle.
Understand the regulatory requirements that apply to your organization, such as GDPR or HIPAA. Ensure that your serverless applications adhere to these standards.
Implement data handling and privacy practices that align with the regulations applicable to your industry. This includes data encryption, access controls, and audit trails.
Develop a robust incident response plan that outlines the steps to take in case of a security breach. Ensure that your team is well-prepared to respond swiftly and effectively.
Regularly back up your serverless data and configurations. Establish a disaster recovery plan to minimize downtime and data loss in case of unexpected events.
Media Contact:
Company Name: Claight Corporation
Contact Person: Louis Wane, Corporate Sales Specialist – U.S.A.
Email: sales@expertmarketresearch.com
Toll Free Number: +1-415-325-5166 | +44-702-402-5790
Address: 30 North Gould Street, Sheridan, WY 82801, USA
Website: https://www.expertmarketresearch.com

WhatsApp us